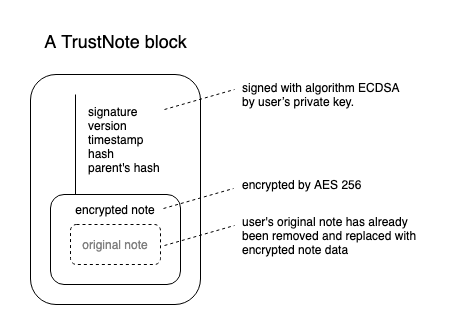
Every note was encrypted and was signed with user’s private key, we call it a TrustNote block.
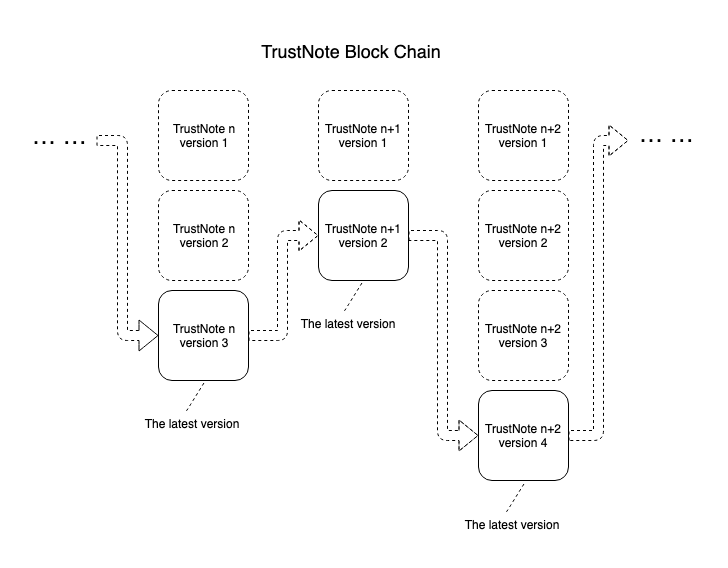
And, all the blocks build a virtual block-chain, looks like this:
Secure Encryption Algorithm
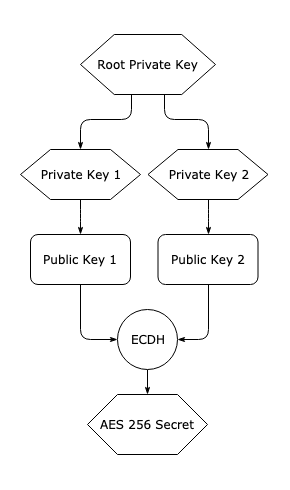
TrustNote encrypt notes by AES-256 encryption algorithm. The AES-256 is currently the most secure encryption algorithm recommended by the US military. The diagram below shows the process how TrustNote generates an AES-256 secret.
TrustNote generates a globally unique private key for every user by the same algorithm as Bitcoin generating a private key, and helps users back up the private key via mnemonic.
The security of Bitcoin is absolutely trustworthy, and so is TrustNote's private key.
TrustNote strongly encrypt notes by AES-256 encryption algorithm before they were synced with others.
Therefore, no matter what type of network eavesdropping, attackers will get nothing while the notes were transmitting over the network.
TrustNote has the ability to promise you that nobody except yourself would know what you noted.
TrustNote signed notes with ECDSA algorithm by user’s private key. If a TrustNote block coming from network fails to pass the signature verification, this block will be discarded. So, even if the storage server was hacked, it is impossible to tamper with any of your notes by attackers.
To protect user’s private key, TrustNote encrypts the mnemonic(for generating/restoring deterministic private key) multiple times with AES-256 encryption algorithm by a password user set.
TrustNote does not have any centralized servers. All your notes were saved on peer-to-peer network and synced by hubs like Github or ipfs all over the world.
TrustNote has the ability to keep notes synchronizing with multiple third-party servers and multiple devices in real time by block-chain technology.
Comparing with traditional network applications, there is no registration required, no sign in required.
But the most important thing is that you have to keep your private key mnemonic in a safe place.